VPNs have been getting more and more buzz in the last couple of years. This is facilitated by the harsh laws of some countries, and the pandemic, which forced people to work from home. But not everyone is familiar with the technology as a whole, let alone such aspects as its individual protocols.
In this article, we’ll talk about just that. We will find out what protocols are, how they differ, compare them with each other and help you choose the most suitable option.
What is VPN
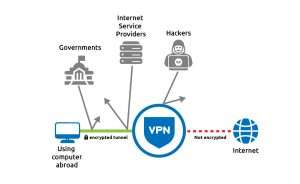
Virtual Private Network (Private Virtual Network) is an extension to a public network that allows you to simulate another network on top of an existing one, to which a limited number of devices can connect.
Usually a ” virtual ” connection is formed between the local computer and the server. The connected systems then enjoy the benefits of a private network. The level of trust in it increases many times due to the traffic protection mechanisms used. And this is despite the low level of trust in the network on which the VPN is based. Once connected to a VPN, you can manage secure files that are accessible only to members of the network, hide outgoing traffic and encrypt it.
Top VPN Use Cases
- VPN was originally developed for offices and large corporations so that employees can connect to the corporate network and work remotely using mobile devices and home computers. They are protected by tunneling technologies.
- Then these features began to be used to bypass various kinds of blocking. For example, regional restrictions from services like Pandora, Hulu, Amazon and Tidal. Or blocking by the state, prohibiting visiting certain resources in connection with the current legislation.
- Also, with the help of VPN, secure communication channels between remote offices are built. For example, if a company is headquartered in London and one of its branches is in Wales, then a VPN will be required for their secure (third-party tamper-proof) data exchange.
What is a VPN protocol?
The VPN protocol is the software foundation upon which any VPN service is built. It describes the format for organizing a connection, data exchange within a private virtual network, and other aspects of the software.
The choice of protocol determines what tasks will be solved with the help of it, how effectively they will be solved, how safe and fast it will be, etc. There are several VPN technologies, so there are some disagreements when choosing the appropriate services and when setting up virtual private networks.
What are the criteria for evaluating VPN protocols?
Each protocol has its own set of characteristics, based on which you need to choose the right one for yourself. Among them:
- Supported platforms – protocols can be quite specific and function exclusively on one or two operating systems. Others support all available operating systems at once.
- Supported Networks – Not all protocols work on identical networks. Some VPN services only offer their services in specific countries due to technological restrictions imposed, including by government agencies.
- The speed of work also depends on the architecture of the protocol. There are those that transfer data faster on mobile devices. There are those that show peak performance only on the scale of large corporate networks.
- Security – The protocols implement encryption and other data security mechanisms in different ways. Therefore, depending on the tasks set, it is necessary to choose a technology that is least susceptible to attacks that are common for it.
Now, from a general description of formats and characteristics, let’s move on to specific technological solutions and their features.
Briefly about existing protocols
To begin with, let’s briefly go over the protocols that we will consider in the article.
- OpenVPN is a balanced option. It is faster than the others and is much less susceptible to attacks from intruders. Top VPN services base their products on this protocol.
- L2TP/IPsec is similar to OpenVPN in many ways. Moderately fast, moderately safe. But this “in moderation” just spoils everything. This does not mean that it should be feared or that it somehow seriously jeopardizes your online privacy. For non-critical tasks, it will be enough with the head. But keep in mind that this protocol is inferior in security to OpenVPN. In the current situation, it is needed as an alternative in case a more suitable protocol is not available.
- IKEv2/IPsec is an alternative to the above protocols, adapted to work on mobile devices. Its advantage lies in the ability to quickly reconnect to the network after a signal loss. This can happen on the zero floors of shopping centers, in tunnels, subways and other places with insufficient “permeability”. IKEv2 is fast, but does not work on all platforms and is difficult to set up.
- SSTP is developed by Microsoft and only works with Microsoft software. Setting it up on third-party operating systems is too complicated, and not everyone wants to deal with technology corporations in such a matter as a VPN. If the involvement of Microsoft is not embarrassing, and Windows is installed on the computer, then this will be a tolerable choice.
- PPTP is another product. An obsolete protocol that is no longer used globally. Useful only in the absence of alternatives.
- WireGuard is a promising new product, similar in many respects to OpenVPN, but overtaking it in all respects (from file transfer speed to the sophistication of encryption methods).
- SoftEther is another modern VPN standard. Fast, fault-tolerant, providing good encryption.
Next, we will analyze each protocol in more detail. Let’s get acquainted with the principles of operation, the degree of security, performance and other aspects of VPN technologies.
OpenVPN
The gold standard among current VPN protocols. Good on all fronts:
- It is universal. It can be used for many purposes, whether you need a virtual “office” protected from prying eyes, or a secure tunnel to connect to blocked resources.
- OpenVPN was created by an independent development team from OpenVPN Technologies. The main advantage of the protocol is its open source code. He owes his wild popularity. The open source entity has helped this technology pass dozens of independent audits from security firms. This was helped by custom encryption methods, support for SSL and AES-256-GCM algorithms.
- It also delivers faster data transfer rates than the competition. Many services that base their VPN servers on OpenVPN provide the transfer of encrypted content at speeds up to 2000 Mbps.
- OpenVPN uses TCP and UDP technologies, thanks to which the standard can be used as an alternative for other protocols when the described standard is blocked on the provider’s side. It also works stably and loses its connection to the Internet less often than others (TCP support also helps in this).
To configure and run OpenVPN, you need a client, that is, software adapted to work with the protocol. You will not be able to use the built-in system tools. Fortunately, there are enough client applications that support this technology. And they are available on Windows, macOS, Linux, iOS, and Android. Depending on the number of connections, OpenVPN may be free, but business customers will have to pay.
The protocol is under active development, constantly acquiring updated security standards and performance improvements.
PPTP
Point-to-Point Tunneling Protocol is an old technology that has long passed into the category of vintage and is now practically not used. It was created by Microsoft in 1999.
The protocol establishes a standard two-channel PPP type connection between devices, and then transfers data through encapsulation using the Generic Routing Encapsulation method. In parallel with this, a connection is made on the TCP port. The first is used directly to transfer information, the second is needed to manage the connection.
PPTP is difficult to set up and manage. For example, due to the need to support two network sessions at once, it is difficult to redirect the signal to the firewall. Security suffers due to GRE specifications and other protocol components.
Despite the presence of support for MS-CHAPv2 and EAP-TLS for user authorization, PPTP remains an insecure VPN protocol and is not recommended for use for serious tasks. You can pick up a key and gain access to a private network in about 23 hours using a specialized online service.
At one time, this technology gained success thanks to the support from Microsoft and the implementation of PPTP in Windows by default. It didn’t require third-party clients or software tools to set up, but with the advent of more reliable alternatives in the vein of OpenVPN, PPTP began to decline in popularity. Now even Microsoft recommends using competitors’ products and stop using PPTP due to its insecurity and instability.
It can still be used to remove regional restrictions, since usually in these cases you do not have to hide traffic and worry about identity theft.
SSTP
Secure Socket Tunneling Protocol is a modified version of PPTP. A kind of add-on to the old protocol, which was supposed to be not only a spiritual continuation of the previously existing technology, but also a correction of all the mistakes made in the “previous version”.
The protocol did not find any noticeable popularity. SSTP’s VPN market share is as modest as the previous iteration of Microsoft’s protocol. But it has the advantage of not having critical security issues. There are no such gaping holes in it, and it is much more difficult to intercept traffic.
SSL encryption helps. When connecting to SSTP, all information is sent through TCP port 443. This approach makes it useful when you need to create secure connections with countries where most VPN services are blocked or prohibited by law.
Numerous tests have shown that SSTP can transfer data at a high speed (if the channel is free) and quickly restore the connection if it suddenly breaks. According to these indicators, the protocol strives for OpenVPN, but falls short due to some limitations of the technology.
SSTP requires a free data channel for normal operation. As soon as a load appears on it (even an insignificant one), the speed of the protocol drops sharply and turns the used VPN service into a real hindrance.
The Secure Socket Tunneling Protocol is available on Windows, Linux, and BSD operating systems, but is supported by a limited number of services. They are hard to find and often more expensive than alternatives. Hence the modest audience of SSTP, which does not plan to grow in the near future due to the advancement of competitors.
IPsec
Internet Protocol Security is not a single technology, but a collection of protocols. Each of them helps to ensure the security of information transmitted over an IP network. In fact, they were not created for organizing VPN connections, this is one of several uses.
The beauty of IPsec lies in its simplified configuration. Due to its architecture and operation at the network level, there is no need to connect third-party clients. VPN based on Internet Protocol Security can be “raised” in all operating systems with built-in tools – through the OS settings. This is its main advantage over OpenVPN.
IPsec security is achieved through two mechanisms.
- Authentication Header – digitally sign each piece of data transmitted over a VPN connection.
- Encapsulating Security Protocol – protects the integrity of the transmitted information and the privacy of protocol users.
IPsec is used in tandem with other technical solutions. Often we are talking about a combination of IPsec and L2TP technologies or about IPsec + IKEv2.
IPsec/L2TP
L2TP was conceived as an alternative to PPTP. The problem was the lack of data encryption mechanisms and authorization methods. Therefore, IPsec was always connected with it. Thus, it was possible to use AES data encryption algorithms. Among the shortcomings of the method, one can single out the difficulties when working with some firewalls, they often block connections on port 500. It is also slow, because it encapsulates the transmitted information twice per session. Other protocols do not.
IPsec/IKEv2
Developed by a team of developers from Microsoft and Cisco, but has several open source variations written by independent programmers. IKEv2 is good with Mobility and Multi-homing Protocol support. This makes it resistant to network changes, it will help smartphone owners stay connected even when going online through a VPN. The connection to the VPN server is not interrupted when you change the router to which the gadget is connected or change the access point while traveling.
IKEv2 supports AES, Blowfish, and Camellia encryption methods. In this regard, it does not differ from L2TP. So they have the same level of protection against attacks from outside. It also consumes less resources than the conditional OpenVPN, and therefore demonstrates a higher data transfer rate. Supported by default on Windows 7 and later, macOS Lion and later, iOS, and select Android smartphones.
WireGuard
New generation of VPN protocols. The developers call it a fast, reliable and easy-to-manage alternative to OpenVPN and other technologies used. No specific opinion on WireGuard has yet been expressed.
It is known that it is based on a bunch of encryption technologies that carefully protect every byte of data sent. Curve25519, ChaCha20, SipHash, BLAKE2 and Poly1305 are used. Moreover, each of the listed types of cryptography takes on a specific task. Let’s say Curve25519 is needed for key exchange, BLAKE2 is engaged in hashing information, and Poly1305 is used for authentication.
WireGuard is lightweight – it only consists of four thousand lines of code. Therefore, developers, if desired, can quickly explore it, analyze it, and even change something. It’s an open standard, just like OpenVPN. This lightness extends to user experience – people are happy to point out that WireGuard is easier to set up than other protocols.
According to the results of benchmarks, WireGuard overtakes the market leaders. The gap between WG and OpenVPN is impressive. 1011 Mbps vs 258 Mbps respectively. With IPsec, the difference is not so big, but it is, and just in favor of WireGuard.
SoftEther
A recent development from the University of Tsukuba. A cross-platform Japanese VPN project that, side by side with WireGuard, is striving to take the first position, beating OpenVPN.
Good compatibility with other VPN technologies. Can work in combination with IPsec, EtherIP, L2TP. Of the additional features it offers: dynamic DNS, built-in packet filter, convenient control panel and control over RPC over HTTPS. And it easily bypasses overly vigilant firewalls that interfere with the normal operation of the network even in safe conditions.
On SoftEther, you can easily move from OpenVPN due to the deep integration of the two services and the clone function in the Japanese protocol.
Just like OpenVPN and WireGuard, it is open source and free.
Comparison table of protocols
Let’s consolidate the new information with the help of a table.
| OpenVPN | PPTP | SSTP | IPsec | WireGuard | SoftEther | |
| Creators | OpenVPN Technologies | Microsoft | Microsoft | Cisco and others | Jason Donfield | University of Tsukuba |
| License type | GNU GPL (open source) | Proprietary | Proprietary | Implementation dependent | GNU GPL (open source) | Apache License 2.0 |
| Supported Platforms | Natively does not support any OS. Third-party customization clients are available for Windows, Linux, macOS, iOS, and Android | Windows, macOS, Linux and iOS without the need to download additional software | Windows without the need to download additional software | Windows, macOS, Linux and iOS without the need to download additional software | Windows, macOS, Linux and iOS without the need to download additional software | Windows, macOS, iOS, Linux и Android |
| Ports used | Any TCP and UPD | TCP 1723 | TCP 443 | UDP 500, UDP 1701 (depends on executable tasks) | Any UPD | Any TCP |
| Encryption methods | The OpenSSL library | The safest available – MPPE | SSL | The most secure available – AES | Curve25519, ChaCha20, SipHash, BLAKE2 и Poly1305 | SSL |
| Vulnerabilities | Not found | MSCHAP-V2 dictionary attacks and Bit Flipping | Not found | Not found | Not found | Not found |
Which protocol to choose?
So far, the favorite is OpenVPN. It has been on the market for a long time and managed to prove itself. Used by top VPN services, works on Android, iOS, Windows, macOS, Linux and even on routers. Is that on the iron will not be able to run. Although the speed of OpenVPN is not amazing, it is enough for comfortable work.
I would give the second place to WireGuard. This is still a dark horse, but with a bunch of bonuses. It outperforms OpenVPN and IPsec in every way, but is not yet as trustworthy as the former. But it’s still a matter of time. It seems that in the near future the alignment of forces in the VPN services market will noticeably correct itself.
Rounding out the top three is IPsec – a perfect balance between performance and availability. True, if you do not take into account the suspicious story of the leakage of data from American intelligence agencies. If you believe them, then IPsec has built-in backdoors that allow you to track traffic transmitted over the IPsec protocol in secret from the sender.
Other technologies were on the sidelines of progress. I do not recommend using them. Only if all other options for some reason were not available.
conclusions
Now you are familiar with the peculiarities of VPN protocols. Based on this information, it will not be difficult to choose the right one (given the fact that the choice is, in fact, small). It remains to “raise” your own server based on OpenVPN or pick up a service in the spirit of the same TunnelBear.